POPI News Updates
De-Identification or Pseudonymisation Examining the Publication of Matric Results under POPIA

Welcome to our latest POPIA training. This edition explores de-identification versus pseudonymisation. We examine why simply removing names doesn't automatically mean data is no longer protected by law.
Data Privacy Roundup 2026 Q1 Edition no 2

Welcome to the latest instalment of our POPIA awareness training. In this edition, we focus on accountability in an increasingly automated world. Whether processing data through chatbots or external vendors, POPIA requires us to remain strictly responsible for the personal information we handle.
KING V™ AND POPIA: TURNING PRIVACY INTO GOOD GOVERNANCE (AND VICE VERSA)

Welcome to the latest instalment of our POPIA awareness training. In this edition, we explore how POPIA and King V™ work together. Good privacy practices aren't a bolt-on—they're part of sound corporate governance, and King V™ shows us exactly how to integrate them.
DATA PRIVACY ROUNDUP FOR 2026 Q1 EDITION 1

Welcome to the first Data Privacy Roundup of 2026. In this edition, we bring you the latest data privacy and protection news from South Africa and around the world—from new breach reporting requirements to major developments in India and the EU.
POPIA AWARENESS TRAINING LEVEL 7

Welcome to the seventh instalment of our POPIA awareness training for employees. In this edition, we focus on the rights of a data subject. POPIA gives every data subject control over their personal information.
DATA PRIVACY ROUNDUP FOR 2025 Q4

In this issue of our data privacy roundup, we discuss what is happening in South Africa and abroad to bring you the latest data privacy and protection news.
POPIA AWARENESS TRAINING LEVEL 6

Welcome to the sixth instalment of our POPIA Awareness Training for employees. In this edition, we are focusing on what happens when personal information is accidentally (or intentionally) exposed, also known as an information security incident, a security compromise or a breach.
DATA PRIVACY ROUNDUP FOR 2025 Q3 (2)

In this issue of our Data Privacy Roundup, we discuss what is happening in South Africa and abroad to bring you the latest data privacy and protection news.
POPIA AWARENESS TRAINING LEVEL 5

Welcome to the fifth instalment of our POPIA Awareness Training for employees. In this edition, we focus on privacy notices – what they are, why they matter, and what they must include. These notices are central to POPIA’s transparency requirements.
DATA PRIVACY ROUNDUP FOR 2025 Q3 (1)

In this issue of our Data Privacy Roundup, we discuss what is happening in South Africa and abroad to bring you the latest data privacy and protection news.
UNDERSTANDING THE AMENDED POPIA REGULATIONS

New definitions for ‘complainant’, ‘complaint’, ‘day’, ‘office hours’, ‘relevant body/bodies’, and ‘writing’ were added. These new definitions are important for interpreting the updated Regulations.
DATA PRIVACY ROUNDUP Q2 2025

In this issue of our Data Privacy Roundup, we discuss what is happening in South Africa and abroad to bring you the latest data privacy and protection news.
POPIA AWARENESS TRAINING LEVEL 4

This is the fourth instalment of our POPIA Awareness Training for Employees series. We cover the basic rules for using operators to process personal information on your behalf.
POPIA AWARENESS TRAINING LEVEL 3

This is the third instalment of our POPIA Awareness Training for Employees series. We cover the basic requirements for securing electronic and physical personal information records.
DATA PRIVACY ROUNDUP Q1 2025
In this issue of our Data privacy roundup, we discuss what is happening in South Africa and abroad to bring you the latest data privacy and protection news.
DATA PRIVACY AND CONSUMER RIGHTS

The Protection of Personal Information Act (POPIA) and the Consumer Protection Act (CPA) are two important South African laws designed to protect data subjects and consumers. While they address different areas – data privacy and consumer rights – they often intersect in ways that significantly impact how businesses operate and how consumers are protected
DIRECT MARKETING IN SOUTH AFRICA

Direct marketing has long been a contentious topic in South Africa, often sparking frustration over unsolicited phone calls and emails. With the implementation of the Protection of Personal Information Act 4 of 2013 (POPIA), the rules governing direct marketing have become stricter, aiming to balance business interests with individual privacy rights. This article discusses the particulars of direct marketing under POPIA and what the latest Guideline from the Information Regulator contains.
POPIA AWARENESS TRAINING LEVEL 2

In level 2 of our POPIA awareness training series, we are looking at instances where you collect personal information, such as customer application forms, employee forms, candidate CVs, and vendor forms.
KNOW YOUR RIGHTS AS A DATA SUBJECT

We are very lucky in South Africa to have so many rights and freedoms. Our right to privacy is enshrined in the Constitution, and POPIA gives effect to that right. It gives you control over your data. But what exactly are your rights as a data subject?
A FINDING ON META’S USE OF PERSONAL INFORMATION FOR TARGETED ADVERTISING

You might recognise the name from the Schrems I and Schrems II decisions that dealt with transferring personal data from the EU to the US. Max Schrems is a co-founder of None of Your Business (NOYB), a non-profit organisation that fights privacy violations by bringing class actions on behalf of data subjects.
DATA PRIVACY ROUNDUP FOR 2024 Q4

In this issue of our data privacy roundup, we discuss what is happening in South Africa, and some data breaches that happened abroad, to bring you the latest data privacy and protection news.
LEVEL 1 POPIA TRAINING

This is the first instalment of our latest series, POPIA Awareness Training for Employees. This series will give you training materials to use in internal POPIA
DATA PRIVACY ROUNDUP FOR 2024 Q4

In this issue of our Data privacy roundup, we chat about some of the data breaches that have happened in South Africa and their impact on South Africans.
WHAT TO CONSIDER BEFORE USING AI TOOLS IN YOUR BUSINESS

Create policies and guidelines for using AI tools within your business. These can include data privacy policies, incident response plans, data subject request procedures,
CONSEQUENCES OF NON-COMPLIANCE WITH POPIA

The Protection of Personal Information Act 4 of 2013 (POPIA) sets the standard for how businesses and individuals process personal information in South Africa,
ISM (INFORMATION SECURITY MANAGEMENT) TIPS FOR SMES – BYTE 10

In our tenth byte, we discuss the final policy statement you should include in your basic ISM policy as an SME: Conduct an Information Security Risk Assessment.
DATA PRIVACY ROUNDUP FOR 2024 Q3

In this issue of our Data Privacy Roundup, we chat about some of the data breaches that have happened in South Africa and their impact on South Africans.
CAN OPERATORS USE DATA TO TRAIN AI AND IMPROVE SERVICES?

An operator is an organisation that processes personal information on behalf of a responsible party under a contract or mandate. Operators follow the responsible party’s instructions and may only make decisions about non-essential means to be used (e.g., what software to use).
JOINT STANDARD 1 OF 2023: IT GOVERNANCE AND RISK MANAGEMENT FOR FINANCIAL INSTITUTIONS

The Joint Standard 1 of 2023 on IT Governance and Risk Management from the South African Reserve Bank provides guidelines for financial institutions to handle IT risks. It highlights the need for strong IT governance to manage
ISM (INFORMATION SECURITY MANAGEMENT) TIPS FOR SMEs – BYTE 9

In this byte, we look at how you should manage and respond to data breaches or incidents. Most people know about the security notification requirements in POPIA
DATA PRIVACY ROUNDUP FOR 2024 Q2

In this issue of our Data Privacy Roundup, we highlight the Information Regulator’s new eServices portal, and their updates to the guidance note for political parties
ENFORCEMENT NOTICES ISSUED BY THE REGULATOR IN TERMS OF POPIA
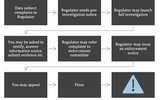
Since last year (2023), the Information Regulator (Regulator) has issued five enforcement notices due to data breaches suffered by responsible parties. The Regulator held a media briefing and summarised the
WHEN POPIA DOESN’T APPLY

When an organisation doing business in South Africa asks ‘Does POPIA apply to us?’ The answer is yes. Even if an organisation doesn’t use personal information to deliver its products or services
Data Privacy Roundup For Q3 2023 - Q1 2024

In this issue of our Data Privacy Roundup, we uncover the significant improvements made by the Information Regulator in enforcing data privacy regulations
ISM (Information Security Management) Tips For SMEs – Byte 8

In this eighth byte, we break down the next policy policy statement you should include in your basic statement you should include in your basic ISM ISM policy – manage third parties.
Are You Being Watched? The Legality Behind Workplace Monitoring

In this post-Covid era, many organisations have adopted a hybrid working model to support their employees. These organisations face the challenge of balancing monitoring employee activities
Navigating The Delicate Balance Of AI And Privacy

As technology rapidly evolves, artificial intelligence (AI) has emerged as a significant innovator across various fields. While AI enhances daily life, it also introduces significant privacy, data security, consent,
ISM (Information Security Management) Tips For SMEs – Byte 7

In our seventh byte, we will break down the next policy statement you should include in your basic ISM policy – information availability. That is, you must ensure that you backed up
Telemarketing In South Africa: Navigating The POPIA Landscape

The telemarketing sector in South Africa is currently undergoing significant regulatory scrutiny. The Information Regulator is taking a strong stance against direct marketers.
What Is It About Personal Information Which Is ‘Publicly Available’ Or ‘In The Public Domain’?

Every so often, a client will say, ‘But that personal information is publicly available, so POPIA does not apply’ … and unfortunately, one has to tell them that this statement is false. POPIA applies to all personal information (unless it is de-identified etc),
More About … Information Matching Programmes

To get a POPIA code of conduct accredited, a POPIA code of conduct must specify appropriate measures for information matching programmes if such programmes are used within the specific relevant sector.
Information Security Management Tips For SMEs – Byte 6

In our sixth byte, we will break down the third policy statement you should include in your basic ISM policy – taking appropriate, reasonable technical and organisational measures to protect the information within your possession or control.
Data Privacy Roundup For Q1 Q2 2023

This is another roundup of the interesting articles, events and guidance released by data protection regulators worldwide, which we have found interesting, informative and valuable from the first and second quarters of 2023.
Do Privacy Rights Exist Concerning The Personal Information Of Deceased Persons

POPIA doesn’t apply to deceased persons’ personal information – end of the story, right? This is the typical answer we receive to this question. However, the answer is a little more nuanced than that.
Gerber V PSG Wealth Financial Planning

Another day, another data breach! Recently (in March 2023), the South Gauteng High Court handed down another interesting judgment related to liability for financial loss caused by cybercrime. To be more specific, in the judgment of Gerber v PSG Wealth Financial Planning 1 , the judge had to deal with the following issue:
ISM (Information Security Management) Tips For SMEs – Byte 5

In our fifth byte, we will further break down the second policy statement a basic ISM policy should include – access control. We will also discuss what implementing this policy statement entails and tips for doing so within an SME environment with limited time and resources.
Data Privacy Round Up For Beginning Of 2023

This is another roundup of the interesting articles, events and guidance released by data protection regulators worldwide, which we have found interesting and informative in the first few months of 2023.
The Impact of AI On The Legal Industry

Lawyers should pay attention to the implications of AI on the legal industry as it will impact how they currently perform services and how they do their work in the future. By automating routine and time-consuming tasks, AI allows lawyers to concentrate on more cost-effective tasks, make better-informed decisions and spend more time on preparation.
What We Think About … Hawarden V Edward Nathan Sonnenbergs Inc

Recently (in January 2023), the South Gauteng High Court handed down a very interesting judgment relating to liability for pure economic loss caused by insufficient or inadequate cybercrime security safeguards.
ISM (Information Security Management) Tips For SMEs – Byte 4

In our fourth byte, we will further break down the first policy statement that a basic ISM policy should include – classifying your information. We will also discuss how to implement this policy statement within an SME environment with limited time and resources.
Data Privacy Roundup For Year-end 2022

This is another roundup of the interesting articles, events and guidance released by data protection regulators worldwide which we have found informative and valuable as of the end of 2022 going into 2023.
How Does POPIA Apply To Litigation Proceedings?

One of the general exclusions for POPIA (as set out in section 6(1)(c)) is that POPIA does not apply to ‘judicial functions of a court’. In one of our ‘tricky areas’, we have asked how far or to what this exclusion would extend.
Handle Data Subject Requests Like A Boss

What is a ‘Data Subject Request’? We made up the phrase ‘Data Subject Request’. It is used in the context of the EU GDPR, but usually to describe requests for deletion or erasure. We use it to describe any instance where a data subject is trying to exercise one of their data-subject rights largely listed in sections 23 to 25 of POPIA.
IsM Tips For SMes – Byte 3

In our third byte, we discuss what we would put in a basic Information Security Management (‘ISM’) Policy for an SME. This gives you a general idea of what policy statements and topics your ISM policy should adopt and address.
Data Privacy Round Up For 2022 So Far

This is another roundup of the interesting articles, events and guidance released by data protection regulators worldwide, which we have found interesting, informative and valuable as of September/October 2022.
Public CCTV Surveillance And Popia – How Do These Two Work Together?

Governments' surveillance of their citizen has seen a massive uptick in the recent years (especially with Covid-19). There is an extreme example of massive public surveillance in China.
Handle Data Subject Requests Like A Boss – Access Requests

What is a ‘Data Subject Request’? We made up the phrase ‘Data Subject Request’. It is used in the context of the EU GDPR, but usually to de- scribe requests for deletion or erasure.
ISM Tips For SMEs - Byte 2

In our next byte, we will discuss documenting the ISM technical and organisational measures you have implemented within your organisation. Remember the series of questions we asked last time (e.g. do you have a data breach response plan
Data Privacy Round Up For 2022 So Far

This is another roundup of the interesting articles, events and guidance released by data protection regulators worldwide
Are Background Checks Legal Under POPIA?

Undoubtedly, background checks are super invasive and require A LOT of personal information. These days, background checks are part and parcel of many application processes
Vetting and Screening Data Subjects Under POPIA

Is it possible to ‘vet’ or ‘screen’ or dare we say ‘profile’ data subjects for their eligibility or suitability for certain goods and services under POPIA?
Data privacy roundup for 2022 so far

We read a lot about data privacy at home and abroad. This is just a roundup of the interesting articles, events and guidance released by data protection regulators...
ISM Tips for SMMes - Byte 1

Why ISM tips for SMMEs? We’ve been doing this for a while and have noticed that this is one area of POPIA compliance that smaller organisations battle with. Keeping any information...
B2B Direct Marketing and POPIA - What's the deal?

There’s been a lot of hoo-hah about POPIA’s impact on direct marketing in the business-to- consumer (B2C) space. But what about POPIA’s impact on direct marketing in the business-to- business (B2B) space?...
To scrape or not to scrape personal information?

The Information Commissioner’s Office (ICO) recently fined Clearview AI Inc £7,552,800 for collecting images of people from the UK from the internet and creating an online database with the images.
Info Wars Episode IX

We discuss how Direct Marketing can still thrive under the rule of POPIA and why telemarketing was left out of discussion under the Act.
How to write contracts that matter

Here’s ten principles to keep in mind and apply when drafting contracts that will better the user’s experience and make it much more palatable when consuming all the information.
Are you mature enough for POPIA

We explain what information governance is and why it is so important to do an information governance maturity assessment before starting a POPIA project.
Does data minimisation spark joy

We discuss the POPIA requirement of ‘minimality’ (as referred to in Section 10 of POPIA) and its benefits for organisations when they implement it.
Hacking data breaches: we need a new breed of compliance officer

We list the knowledge and skill requirements necessary for Compliance Officers to properly manage their organisation’s Information Security and what organisations need for adequate Incident Response Management.
Direct marketing and the dreaded consent

We discuss what Direct Marketing and Consent are, when it’s necessary to obtain consent, when not to and what it should look like.
The C-word

We discuss Consent, one of the six lawful grounds for processing personal information; what it means, in what circumstances it’s not necessary to ask for consent and if you do need to - how to ask and how to manage it.
POPIA compliance and Codes of Conduct

We discuss what a Code of Conduct is, the purpose of a Code of Conduct, and what specific issues should be regulated under a Code of Conduct.
Get the right Operator contracts in place in 6 simple steps

POPIA requires a Responsible party to conclude a written agreement with all its operators. We discuss what an Operator is in terms of the POPIA and provide six steps that you should follow to help you comply with this requirement.
Our top five favorite privacy notices

We discuss the POPIA requirement of ‘minimality’ (as referred to in Section 10 of POPIA) and its benefits for organisations when they implement it.